Overview
Notifuse handles two types of webhooks:- Incoming webhooks - Callbacks from email providers (Amazon SES, Mailgun, Postmark, etc.) that notify Notifuse about email events like bounces, complaints, and deliveries. These are configured automatically when you set up an email integration.
- Outgoing webhooks - HTTP callbacks that Notifuse sends to your server when events occur. This is what this feature page covers.
- Sync contact data to your CRM or other systems
- Trigger workflows in external automation tools
- Build custom integrations and dashboards
- React to email engagement events in real-time
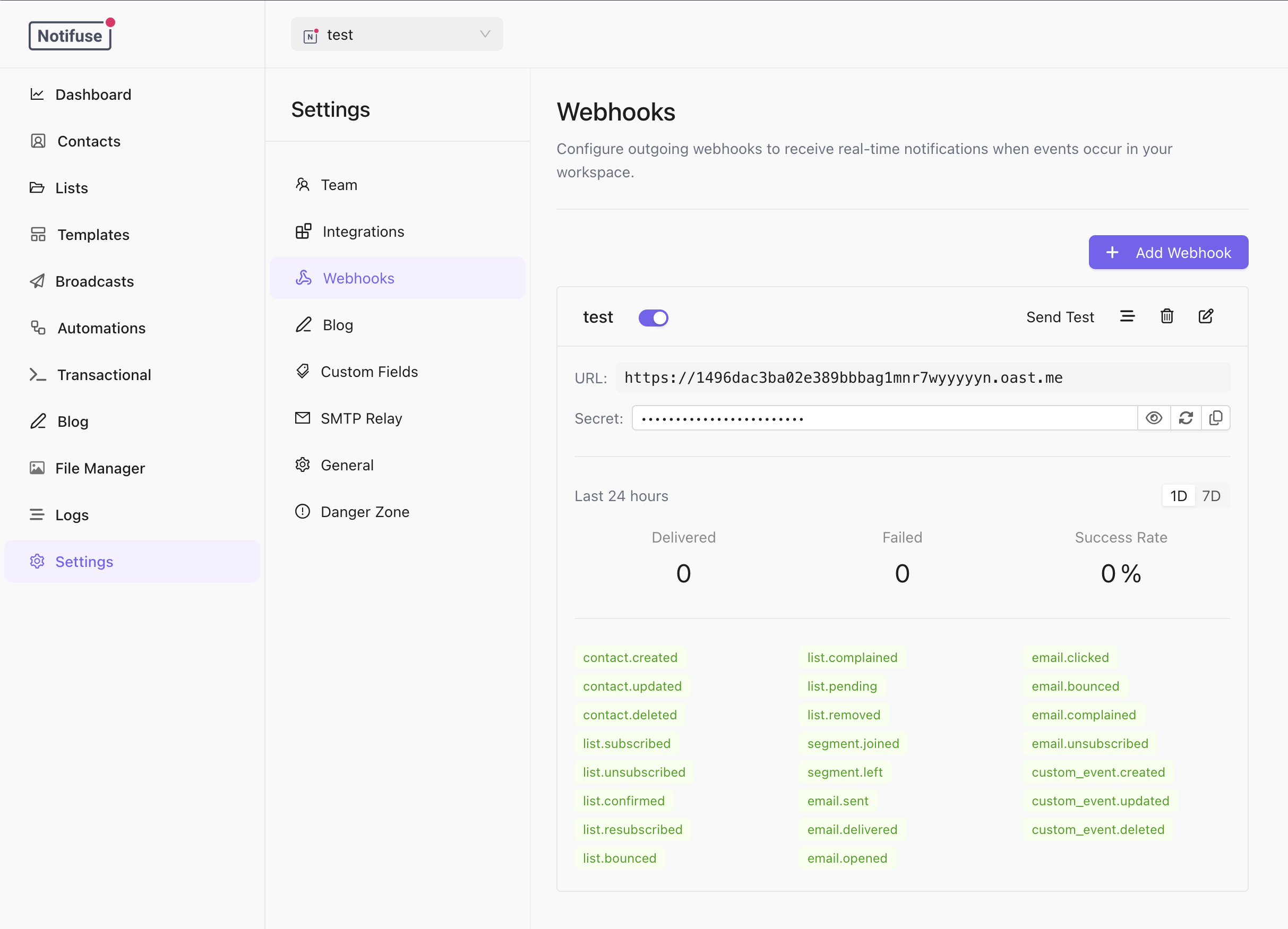
Creating a Webhook Subscription
Create a webhook subscription via the API or the Notifuse console:Available Event Types
Contact Events
| Event | Description |
|---|---|
contact.created | A new contact was added to the workspace |
contact.updated | Contact data was modified |
contact.deleted | A contact was permanently deleted |
List Events
| Event | Description |
|---|---|
list.subscribed | Contact subscribed to a list |
list.unsubscribed | Contact unsubscribed from a list |
list.confirmed | Contact confirmed double opt-in subscription |
list.resubscribed | Previously unsubscribed contact resubscribed |
list.bounced | Email to contact bounced |
list.complained | Contact marked email as spam |
list.pending | Contact subscription is awaiting confirmation |
list.removed | Contact was removed from list |
Segment Events
| Event | Description |
|---|---|
segment.joined | Contact entered a segment (matched segment criteria) |
segment.left | Contact left a segment (no longer matches criteria) |
Email Events
| Event | Description |
|---|---|
email.sent | Email was sent to contact |
email.delivered | Email delivery was confirmed by the recipient’s server |
email.opened | Contact opened the email |
email.clicked | Contact clicked a link in the email |
email.bounced | Email delivery failed |
email.complained | Contact marked email as spam |
email.unsubscribed | Contact unsubscribed via email link |
Custom Events
| Event | Description |
|---|---|
custom_event.created | A new custom event was recorded |
custom_event.updated | A custom event was updated |
custom_event.deleted | A custom event was soft-deleted |
Custom Event Filters
For custom events, you can optionally filter bygoal_types and event_names:
Payload Structure
All webhook payloads follow this structure:| Field | Description |
|---|---|
id | Unique identifier for the webhook delivery |
type | The event type that triggered the webhook |
timestamp | ISO 8601 timestamp when the webhook was sent |
workspace_id | The workspace where the event occurred |
data | Event-specific payload data |
Example: Contact Created
Example: Email Sent
Example: Email Opened
Example: Segment Joined
Verifying Webhook Signatures
Notifuse signs all webhook payloads using the Standard Webhooks specification with HMAC-SHA256.Headers
Each webhook request includes these headers:| Header | Description |
|---|---|
webhook-id | Unique identifier for the webhook delivery |
webhook-timestamp | Unix timestamp when the webhook was sent |
webhook-signature | HMAC-SHA256 signature of the payload |
Verifying the Signature
- Extract the timestamp and signature from the headers
- Construct the signed payload:
{webhook-id}.{webhook-timestamp}.{body} - Compute HMAC-SHA256 using your webhook secret
- Compare with the provided signature
Code Examples
Retry Behavior
Notifuse automatically retries failed webhook deliveries with an exponential backoff strategy.Retry Schedule
Webhooks are retried up to 10 times over approximately 34 hours:| Attempt | Delay After Previous |
|---|---|
| 1 | Immediate |
| 2 | 30 seconds |
| 3 | 1 minute |
| 4 | 2 minutes |
| 5 | 5 minutes |
| 6 | 15 minutes |
| 7 | 30 minutes |
| 8 | 1 hour |
| 9 | 2 hours |
| 10 | 6 hours |
| Final | 24 hours |
Success Criteria
A webhook delivery is considered successful if your endpoint returns HTTP status code2xx (200-299).
Failure Conditions
A delivery attempt fails if:- Your endpoint returns a non-2xx status code
- The request times out (30 second timeout)
- The endpoint is unreachable (DNS error, connection refused, etc.)
Best Practices
Return 2xx Quickly
Return a successful response as quickly as possible. Process the webhook payload asynchronously if needed:Handle Duplicate Deliveries
Webhooks may be delivered more than once in rare cases. Use thewebhook-id header to implement idempotency:
Verify Signatures
Always verify webhook signatures in production to ensure requests are from Notifuse.Monitor Delivery Failures
Use the Notifuse console or API to monitor webhook delivery status:Testing Webhooks
Send a Test Webhook
Use the test endpoint to verify your webhook configuration:event_type parameter is optional. If provided, the test webhook will include a realistic sample payload for that event type. If omitted, a generic test payload is sent.
Local Development
For local development, use tools like ngrok or localtunnel to expose your local server:Notes
- Webhooks require HTTPS endpoints in production
- The signing secret is generated automatically when you create a subscription
- Use
webhookSubscriptions.regenerateSecretto rotate the signing secret - See API Reference for complete endpoint documentation
